Background
I’m sure everyone reading this blog post has had experience with Potentially Unwanted Applications (PUA) or Potentially Unwanted Programs (PUP). You might have recently purchased a new laptop or PC and found that there are applications on it preinstalled that are annoying and unwanted. It really is a subjective topic, as one person might find these programs useful but another might find them irritating and classify them as bloatware. I’ve recently got a new HP laptop that came with various pre-installed OEM software. Some of them are useful like the recovery tools that allow OS reinstalls however I’m not a fan of the analytics and telemetry data that gets sent back without the users consent or in some cases is an opt-out feature. Most of them either don’t provide much value to the end user or just get in the way and are bothersome.
Introduction
The software or applications that are the most troubling are the ones that can not be removed. In this blog post I’m going to talk about one in particular that I noticed deployed by HP called Dynamic Audio. I will be walking through an in depth analysis using various programs and tools that I’ve picked up on over the years investigating how applications on windows function.
HP Dynamic Audio
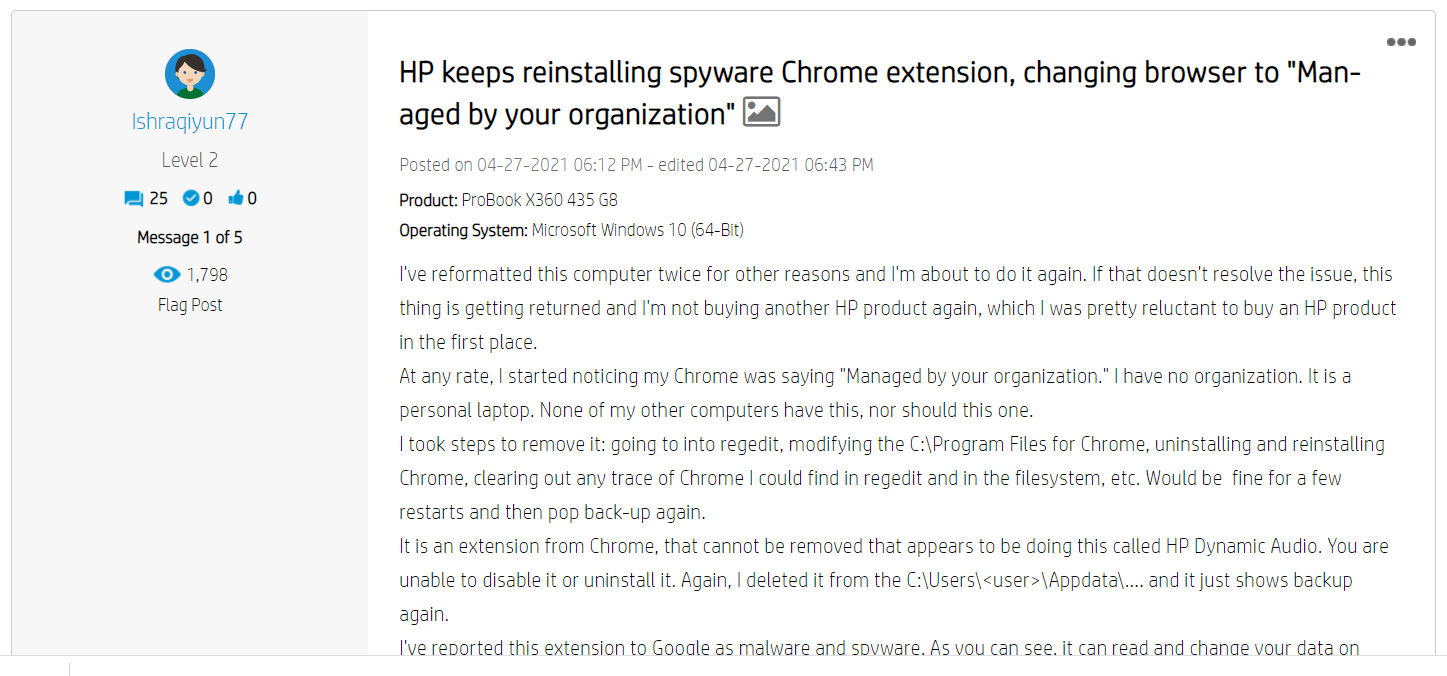
HP Dynamic Audio is supposedly a new AI-based audio experience that tunes output to speech while suppressing background noise. The first thing I noticed is that it pre-installs itself into your Google Chrome browser and it is visible from the sidebar menu. You can see it says “Managed by your organization”
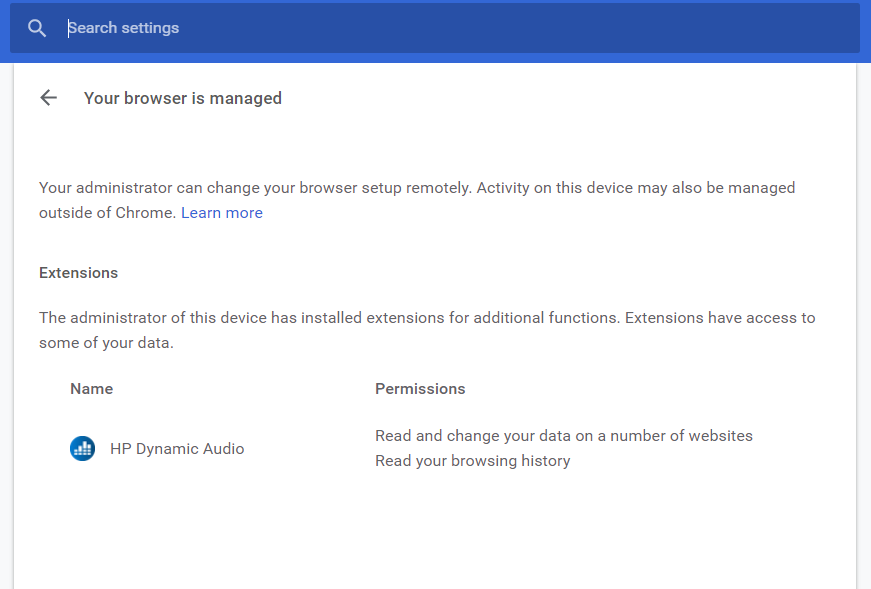
Clicking that button brings you to the management window inside of Google Chrome. Here you can see that HP has taken advantage of this functionality to force install the extension called HP Dynamic Audio. Now there is no way available to the end user to remove this extension from the UI and there are a few steps involved I will explain later including a script I wrote to do it. You can also take note of the permissions granted which allows this extension to read data on a number of websites.
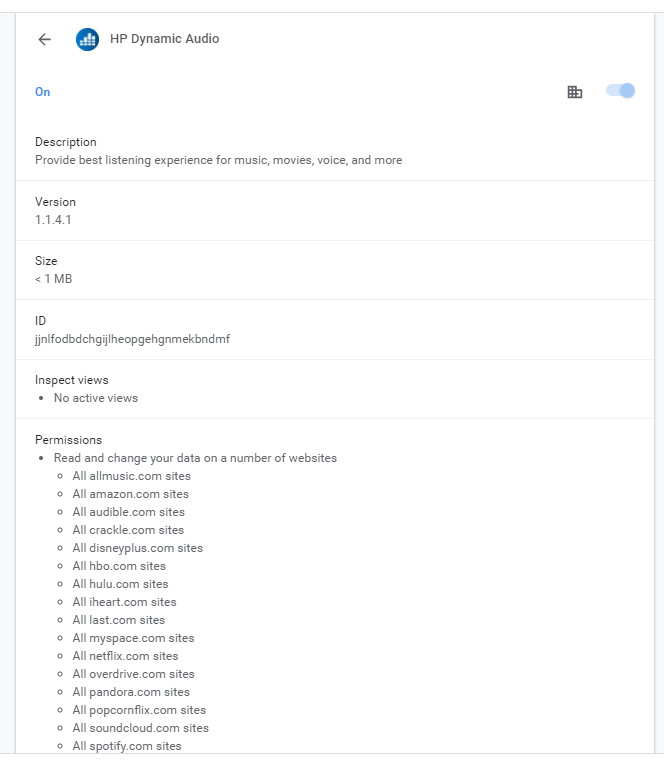
Looking further into the extension we can see the websites it has access to and once again since the browser is in a managed state there is no option to turn this off or remove it from inside Chrome. This to me is unacceptable no matter what the software is. As an end user that owns a device you should have the right to remove or disable software like this especially if it has access to your data.
Removal Attempt
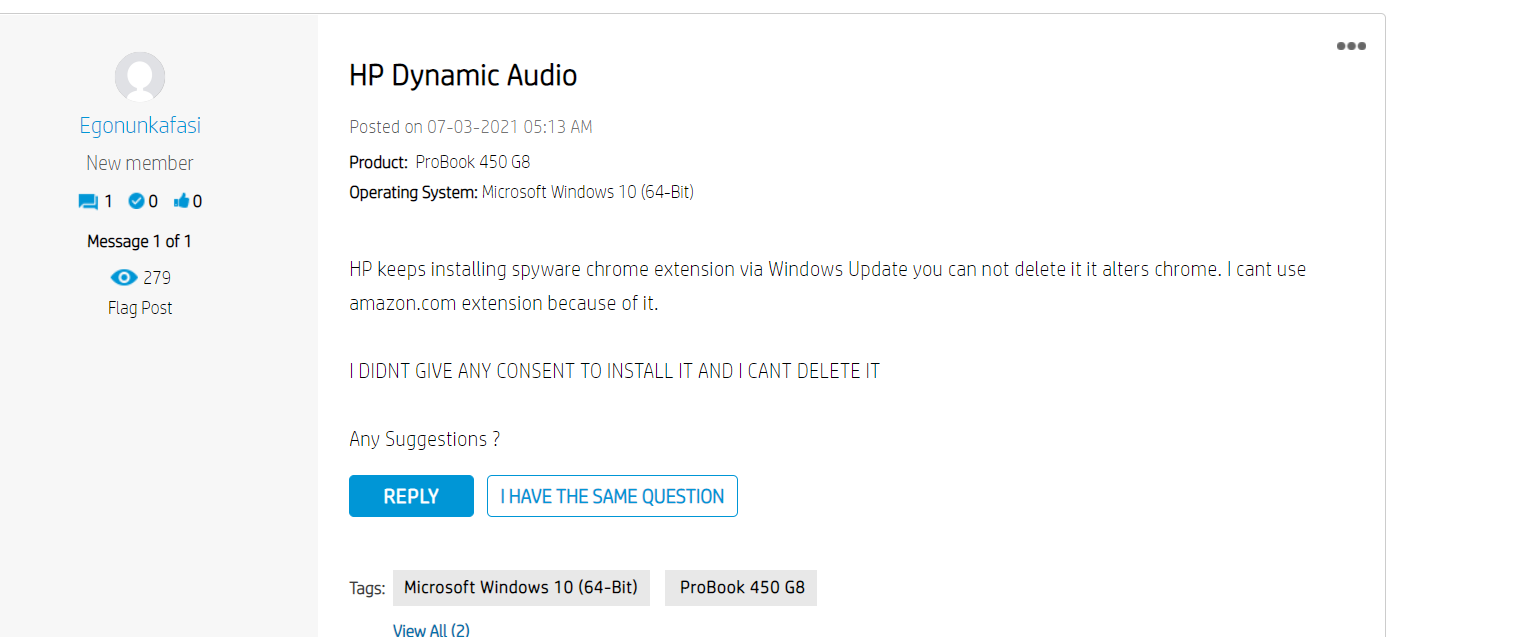
My first attempt to remove this from Google Chrome was to reinstall the browser. Since Chrome has the ability to synchronize settings this wasn’t a big issue for me. However, after a reboot it was back! So I decided to do a bit of googling and found many others in despair.
A simple reinstall and reboot wasn’t going to cut it. I needed to dive deeper into how and what was causing this extension to be force installed.
A deep dive
Google’s own documentation explains how to use the group policy system to enable the auto install of extensions for the use by organisations. This feature is used to enforce policies on there devices. There wasn’t adequate information in the documentation until I found a help centre article on how to stop the Chrome browser from being managed.
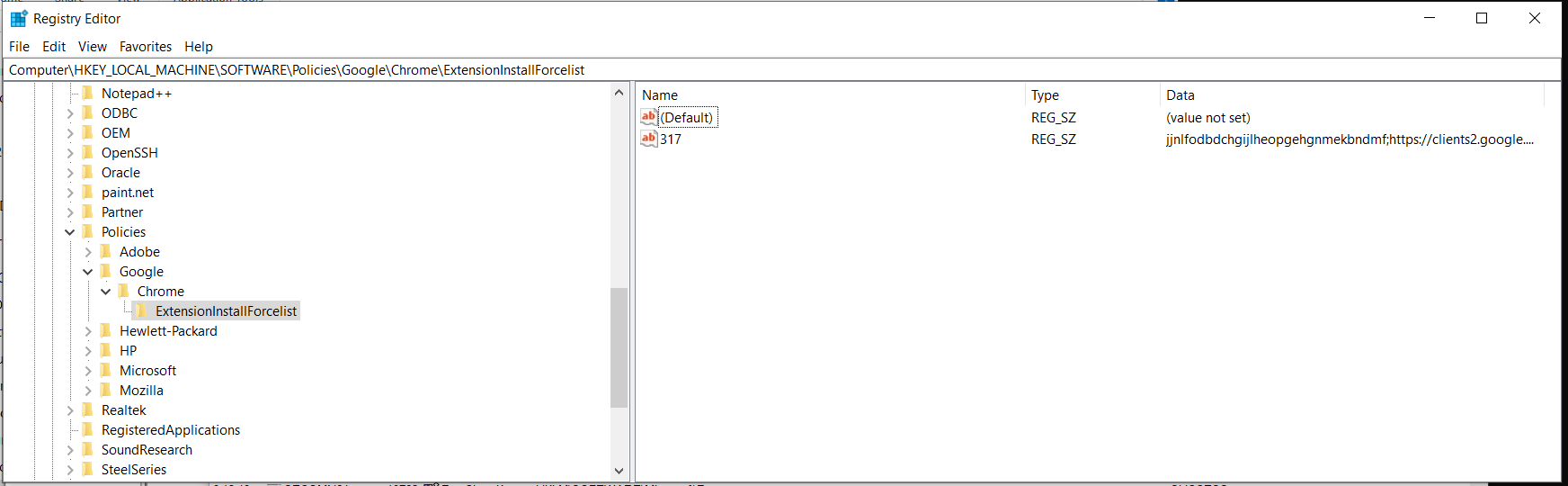
It was evident that whatever application/service/driver HP had installed, was writing to the registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome\ExtensionInstallForcelist
We can see that there is an entry in that key 317 with a value of jjnlfodbdchgijlheopgehgnmekbndmf Looking at extension Id inside of Chrome we can see it matches and this is in fact the entry for ‘HP Dynamic Audio’.
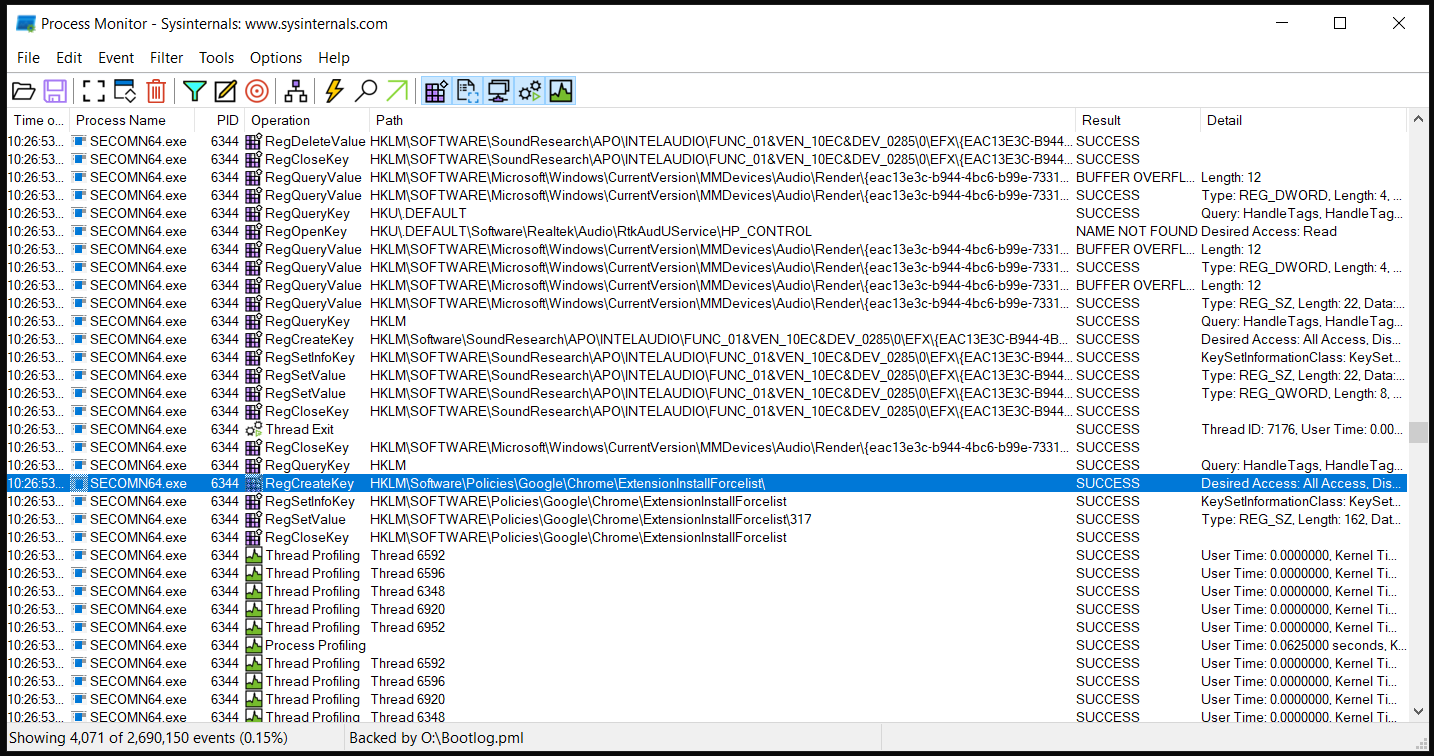
Removing this registry entry wouldn’t fix the problem as it will get repopulated upon reboot. So there must been an application running that is writing to this address. In order to uncover this I used a program called Process Monitor by Mark Russinovich. I’ve used this tool in the past to analyse the behaviour of certain malware to see their affects on the OS. It allows you to monitor API calls and events that occur on Windows and for this case it was perfect.
Searching for that specific registry key path it uncovered a process called SECOMN64 which was accessing and creating key entries. Bingo we got something now!
One of the benefits and great functionality of this tool is it allows you to see the stack at the time of the API call.
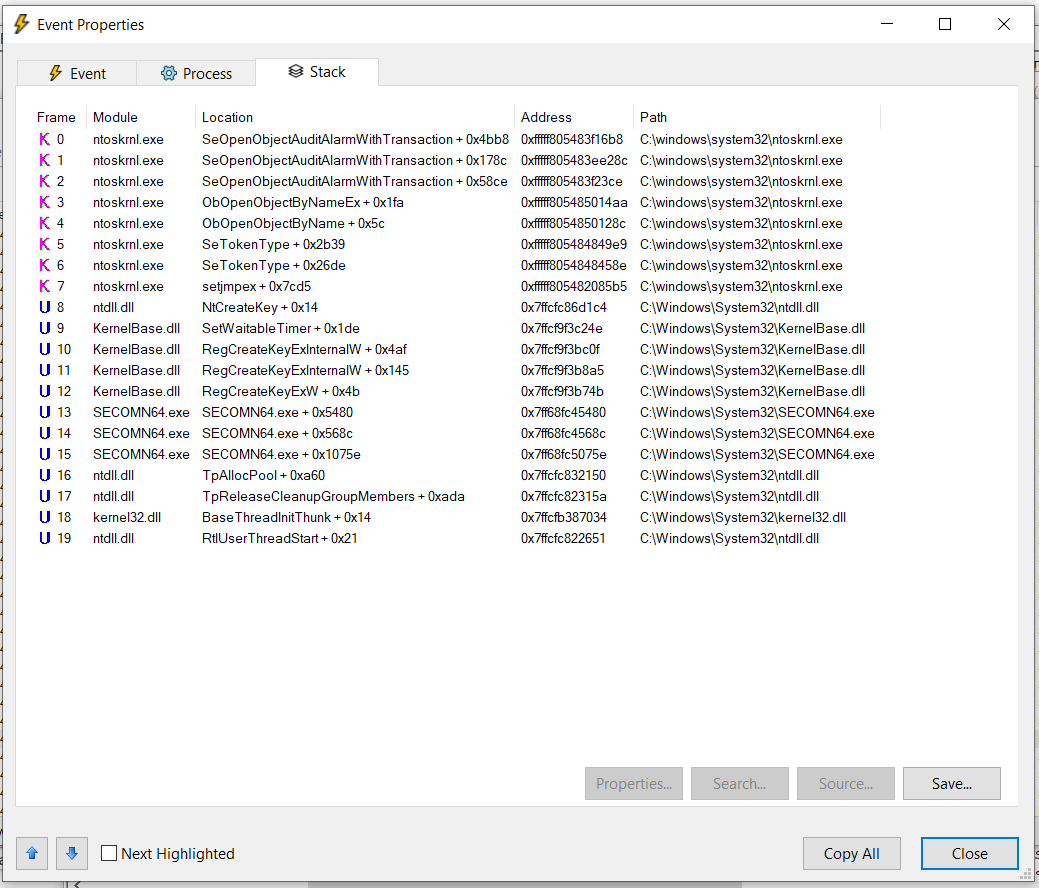
Here we can see the SECOMN64 executable calling into the KernelBase library querying the RegCreateKeyExW WINAPI. We can follow the stack lower into the Windows Kernel but there is no need.
Now that we have the file path to SECOMN64.exe we can throw it into a dissembler and reverse engineer what is going on.
Interactive Dissembler (IDA)
The Interactive Disassembler (IDA) is a reverse engineering tool that can be used to dissect executables. It has a powerful dissembler that can take machine processer instructions and generate pseudo readable source code for you to understand and reverse engineer application functionality.
Looking at the strings inside the executable you can see there is the same extension id that we found in the registry key. There are also other strings there which indicate that there is some functionality to classify websites the user is currently on and also one called YoutubeCategoryClassifications which is interesting.
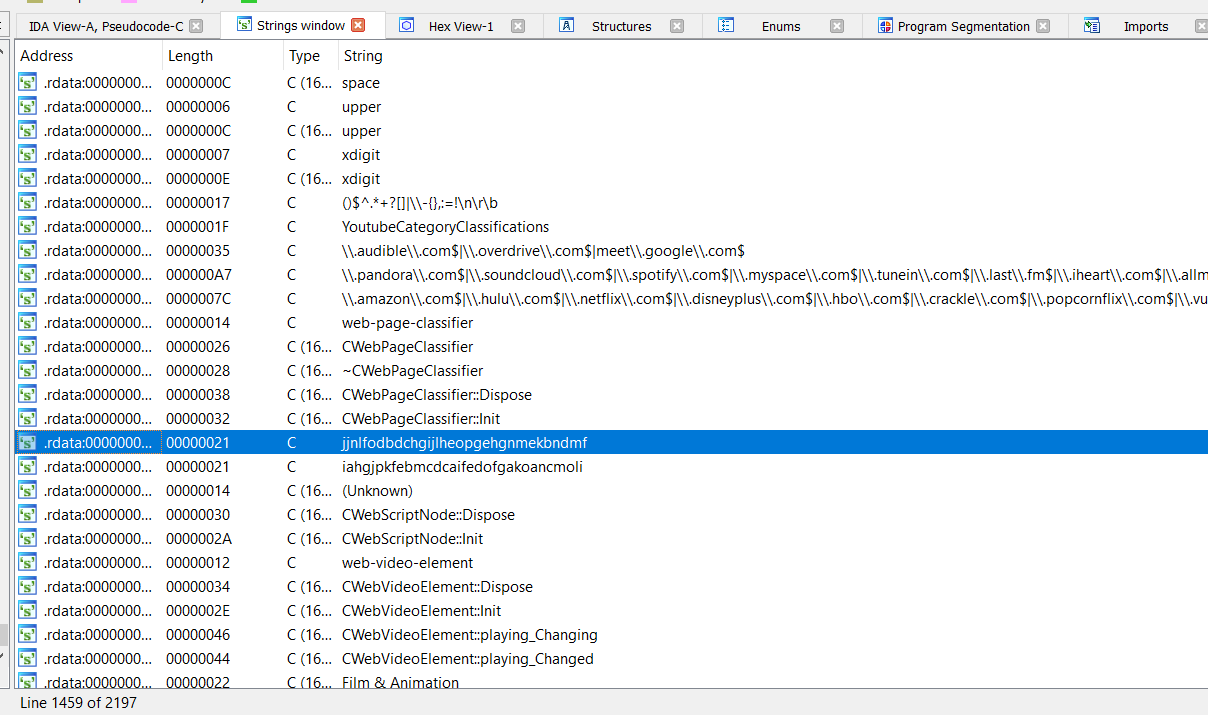
There is also some amusing debug error entries about force install failing.
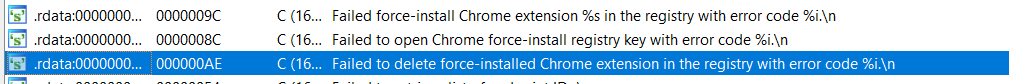
Cross-referencing the string for the extension Id we can find the function responsible for its creation. Alternatively using the stack trace we can find the location of the exact call by offsetting from the loaded image base. To find or change that is via the Edit -> Segments -> Rebase program.
The PE Image executable inside of IDA was loaded at 0x140000000 therefore we simple add the offset shown in the stack trace window.
0x140000000 + 0x5480 = 0x140005480
This will bring us to exactly where we need you can see those WinApi calls we caught with Process Monitor. RegCreateKeyEx RegSetValueExW
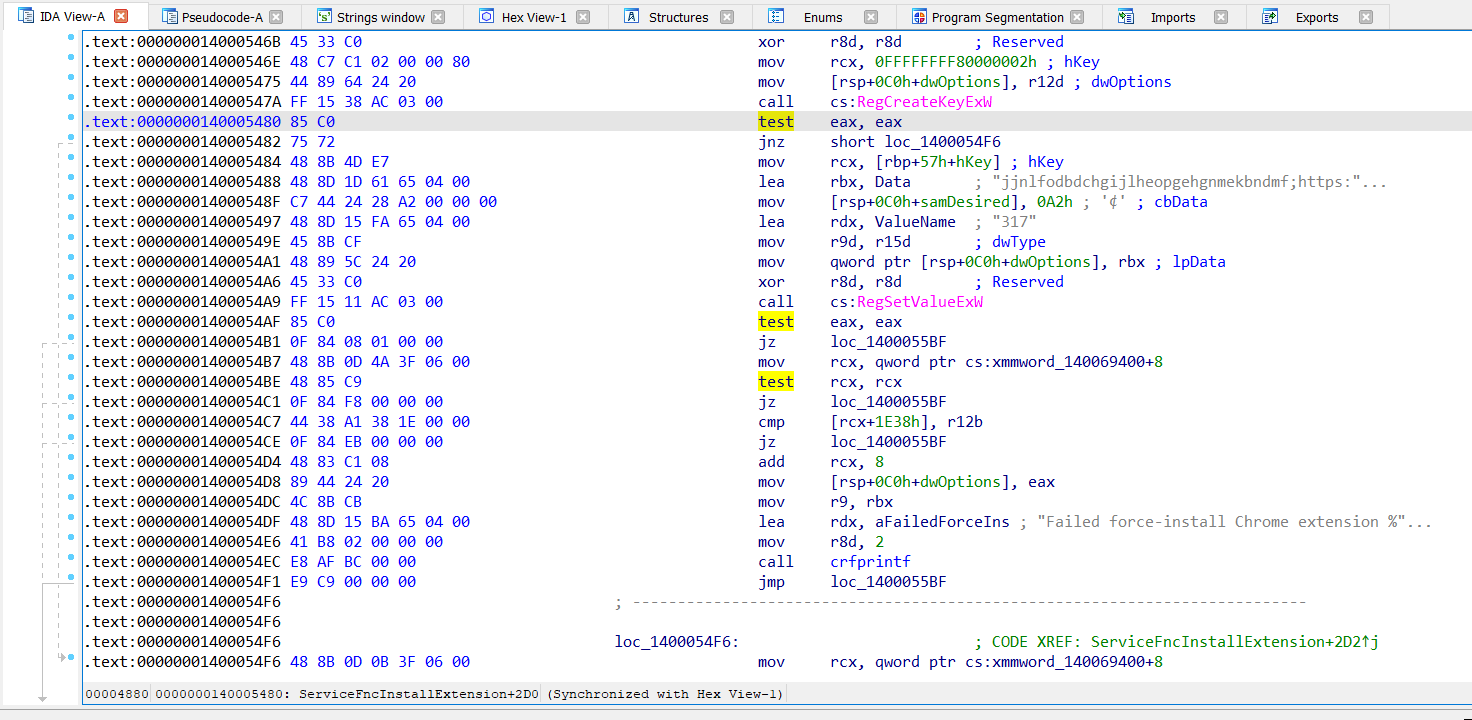
Hitting F5 in IDA allows us to view the x86-64 assembly in a human readable pseudo code.
We now know what process is causing the install of this extension and what it’s doing to do that utilizing the ExtensionInstallForcelist ability inside of Google Chrome.

Windows Services
Looking at the Windows Services we can find a match for that executable and it seems to be named Sound Research SECOMN Service.
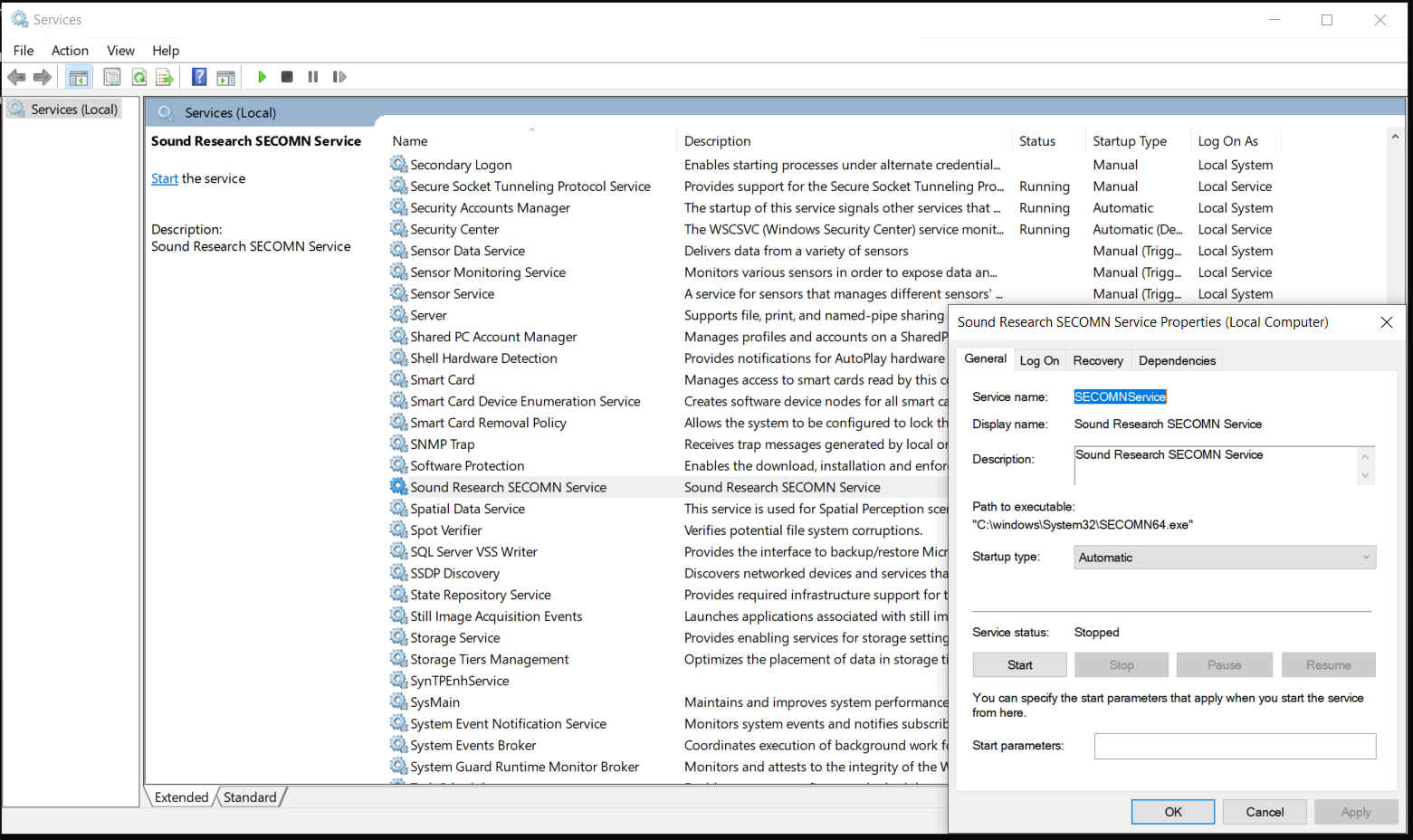
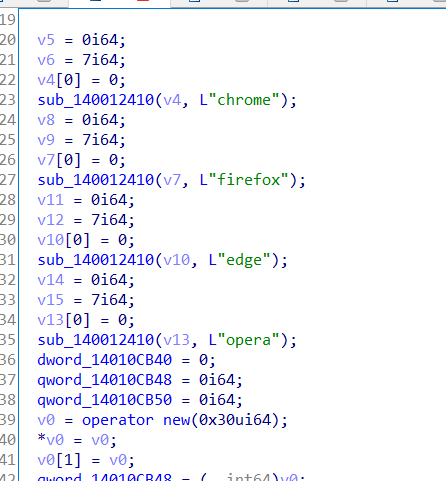
At the time of writing this blog post, setting the service Startup type to Disabled and deleting the relevant registry keys in the registry seems to remove this browser extension from being force installed into Chrome. I may write a subsequent post at some point in the future if I uncover other interesting information. Something that stood out to me whilst looking at another service in the same driver bundle was that there is some activity to suggest other web browsers might be impacted in a similar way.
Conclusion
It is disappointing how manufactures go about installing PUAs onto user machines and there should always be a choice to the end user to remove or disable what they do not want on their computers. I hope this deep dive gave some insight into how you may investigate activity of applications using tools such a Process Monitor and IDA.
I have created a windows batch script that automates the process of removing the Managed state of Chrome and disabling the service responsible for persisting the extension install below.
References & Resources
- https://support.google.com/chrome/a/answer/187202?hl=en
- https://support.google.com/chrome/a/answer/9844476?hl=en
- https://sites.google.com/site/lock5stat/offline-use/installing-for-all-users
- https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
- https://hex-rays.com

