Reading Time: 7 minutes Concept A while back I was working on a add-in/plug-in for a software that would enhance it’s functionality. I found that the easiest and most pain free way of loading arbitrary code was via a method referred to as DLL ‘proxying‘ or ‘hijacking‘. This method is unfortunately abused and most commonly used in malware prompting …
Category Archives: Reverse Engineering
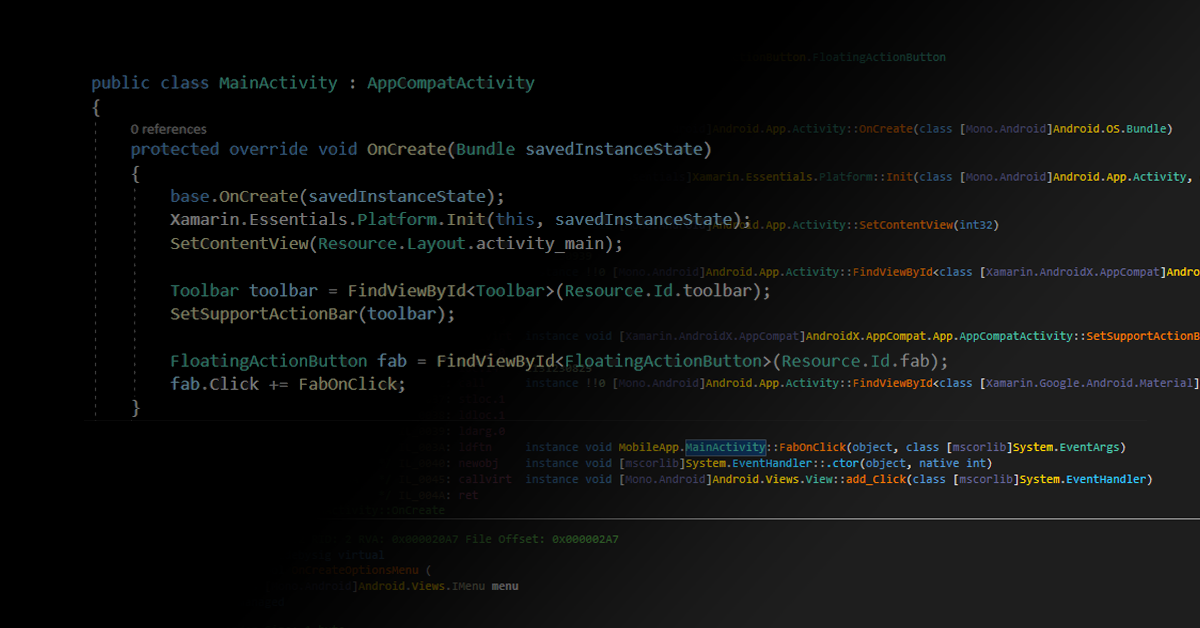
Unpacking Xamarin Android Mobile Applications
Reading Time: 5 minutes Recap & Introduction In my previous post I detailed how to decompile .NET code and explained how this was possible given the nature of the .NET platform. This post will walk you through how to unpack and decompile android mobile applications built on the Xamarin platform. Additionally I will also talk about a utility app …
Continue reading “Unpacking Xamarin Android Mobile Applications”
Decompiling .NET Code
Reading Time: 7 minutes Introduction When you build an native application your written source code gets compiled down to a language that can be understood by the target processor you’re developing for (eg. ARM), this is referred to as machine code or assembly. Decompiling such applications are not possible as there is information that gets lost during the compilation …
Uncovering HP’s Potentially Unwanted Applications
Reading Time: 6 minutes Background I’m sure everyone reading this blog post has had experience with Potentially Unwanted Applications (PUA) or Potentially Unwanted Programs (PUP). You might have recently purchased a new laptop or PC and found that there are applications on it preinstalled that are annoying and unwanted. It really is a subjective topic, as one person might …
Continue reading “Uncovering HP’s Potentially Unwanted Applications”